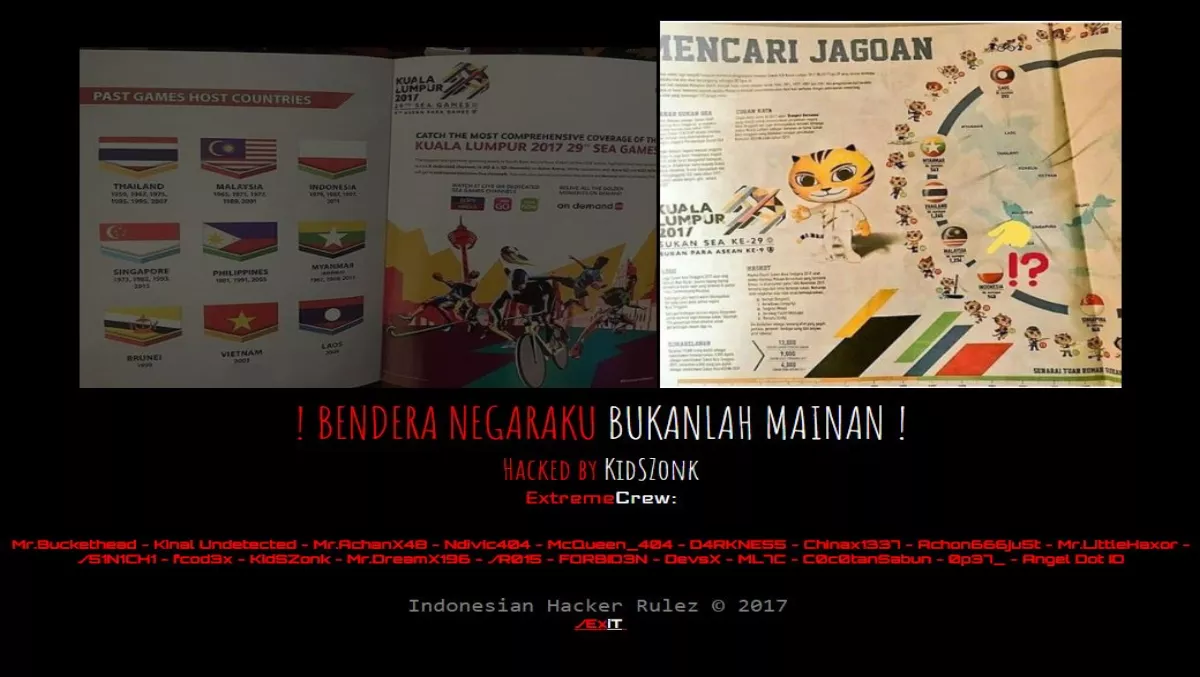
Upside-down flag prompts hack against Malaysian websites
Malaysia's Computer Emergency Response Team (MyCERT) has issued a report about several hacks against Malaysian websites, which include information leaks and Distributed Denial of Service (DDoS) attacks.
According to reports, Indonesian hacker KidSZonk and group ExtremeCrew are behind the attacks. The reports suggest the attacks are in response to an error in the Kuala Lumpur SEA Games 2017 booklet, which printed the Indonesian flag upside down.
The hackers used the words "Bendera Negaraku Bukanlah Mainan", which loosely translated, means 'my country's flag is not a toy'.
The hacks may have hit Malaysian government-owned websites, including one owned by the SEA Games Committee.
The website appears to show a picture of the upside down flag and the hackers' usernames on the website.
MyCERT says that system administrators should take the following steps to secure their networks:
1. Organizations are recommended to apply defense in depth strategy in protecting their networks. Firewalls, intrusion prevention systems (IPS), network and host based intrusion detection systems (IDS) can prevent and log most of the generic attacks. Make sure systems, applications and third party add-ons are updated with latest upgrades and security patches. 2. If you're running older versions of operating systems or software, make sure they are upgraded to the latest versions as older versions may have some vulnerability that can be manipulated by intruders. Aside from that, please make sure that your web based applications and network based appliances are patched accordingly. You may refer to your respective vendors' websites for the latest patches, service packs and upgrades. 3. If you do not prepare for a DDoS incident in advance, contact your ISP to understand the DDoS mitigation it offers and what process you should follow. If the risk of a DDoS attack is high, consider purchasing specialized DDoS mitigation products or services. 4. Harden the configuration of network, OS, and application components that may be targeted by DDoS. Whitelisting and blacklisting IP address during DDOS is very useful to mitigate the attack to certain extend 5. Make sure Anti-virus software that are running on hosts and email gateways are updated with the latest signature files and are enabled to scan all files. 6. Make sure that your systems are configured properly in order to avoid incidents such as information disclosure, directory listing that are caused by system misconfiguration. 7. Make sure loggings of systems and servers are always enabled. System Administrators are advised to read and monitor the logs on daily basis. 8. Perform regular backups of all critical information to limit the impact of data or system loss and to help expedite the recovery process. Ideally, the backup must be done daily, on a separate media and stored offline at an alternate site. 9. Organizations are recommended to regularly conduct vulnerability assessment and penetration testing on their systems. 10. Report security incidents to relevant authorities or to CERTs/CSIRTs in your constituency for immediate remediation and mitigations.


