
UPDATED: Orvibo & Arlo smart home products patched to prevent attacks
The security of smart home devices is once again under the spotlight this week, as two different device manufacturers come under fire for major vulnerabilities. Arlo and Orvibo devices are at risk of exposing data and letting attackers compromise devices such as security cameras.
The Orvibo data leak
A company called vpnMentor discovered an open database of more than two billion logs linked to Orvibo Smart Home products. Those logs include personal information including email addresses, passwords, devices, recorded conversations, IP addresses, account reset codes, and the precise geolocation of affected devices.
Logs were found for users in China, Japan, Thailand, the US, the UK, Mexico, France, Australia, and Brazil.
Orvibo devices aren't just used in homes – they're also used in businesses and hotels.
On July 5, Orvibo released a statement to media apologising for the leak.
"Once we received this report on July 2nd, Orvibo's RD team took immediate actions to resolve security vulnerability," the statement says.
"As an IoT company, Orvibo attached great importance to user data security. We have taken effective solutions to resolve it:
1. Resolved security vulnerability.
2. Upgraded encryption mechanism of password.
3. Upgrade the protection on users account and password resetting.
4. Strengthening cooperation with professional cyber security companies to improve our system security."
Thanks for vpnMentor's research report. Due to their timely report, there has no any [sic] users' data leak until now. Orvibo keeps improving users' data protection and information security in the long term."
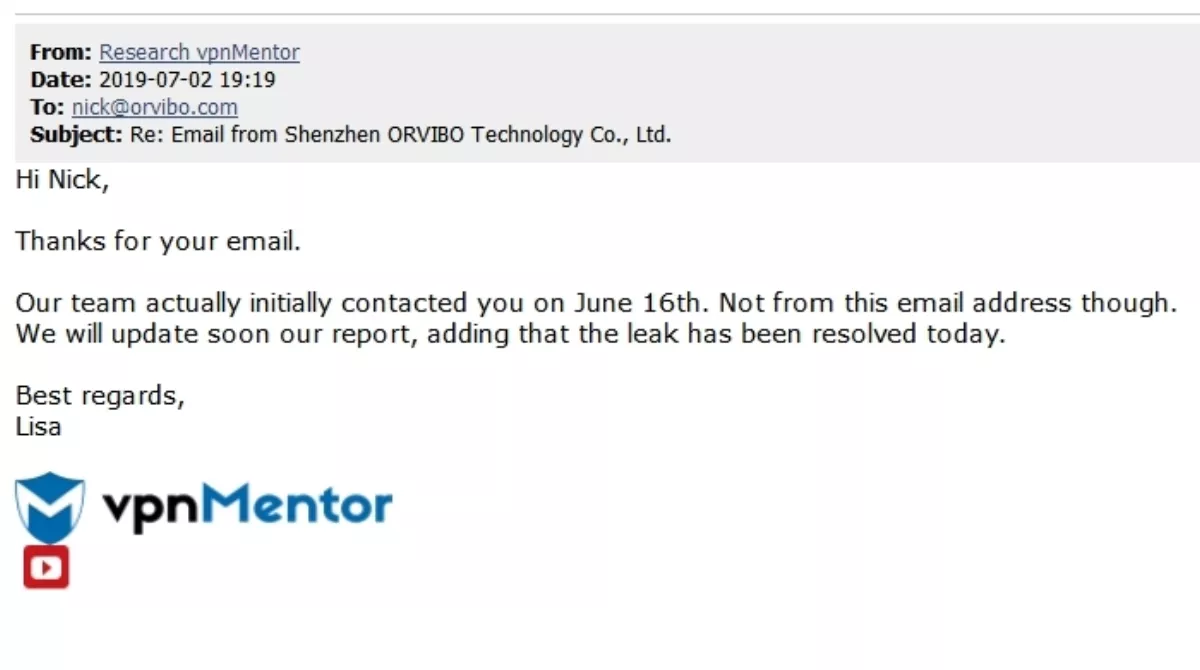
vpnMentor claims it initially contacted Orvibo on June 16, but it seems that ORVIBO was only made aware of the issue when vpnMentor made it public on July 2. Orvibo provided the following screenshot to media that proves the initial date vpnMentor made contact.
"This just highlights the sheer magnitude of endless possibilities open to poor security on IoT devices," comments ESET cybersecurity specialist Jake Moore.
"By not looking after personally identifiable and confidential data at the back end of a website has just as much risk attached as not using a password at all. Criminal groups may have been aware of this vulnerability, but it is unknown if anyone has taken advantage of this flaw yet and I'd hope it would be patched quite quickly now it is out. What a criminal hacker could do with this goes as far as their imagination will take them.
"The best thing now for people affected is to make sure their smart device passwords are changed immediately to something long and complex along with other accounts where the same password may be reused. However, if cybercriminal gangs are already in and watching their every move before a patch is installed, they may as well pull the plug on the device until it is fixed.
VpnMentor recommends that users:
1. Secure servers.
2. Implement proper access rules.
3. Never leave a system that doesn't require authentication open to the internet.
Arlo systems vulnerable to attack
Tenable research has disclosed several security flaws that affect Arlo security systems, which include baby monitors and wire-free cameras.
Those vulnerabilities could allow attackers to take complete control of the devices connected to the base station, so that they could watch private video footage and potentially tamper with video feed.
The flaws were found in Arlo's base stations (firmware version 1.12.0.1_27940) which are used to power the company's various products.
Arlo has released VMB3010 and VMB4000: 1.12.2.3_2782; VMB3500 and VMB4500: 1.12.2.4_2773; VMB5000: 1.12.2.3_59_4a57cce to address the vulnerabilities. Tenable urges users to confirm their Arlo base stations have been updated to this latest version.


