GitHub to boost security tracking for developers' projects
GitHub has unveiled security improvements to its coding platform, which will allow developers to track which dependencies are associated with public security vulnerabilities.
The new plans were revealed at the annual GitHub Universe developer conference, which is taking place in San Francisco this week.
According to GitHub, software builders may rely on some of the millions of open source projects on the platform.
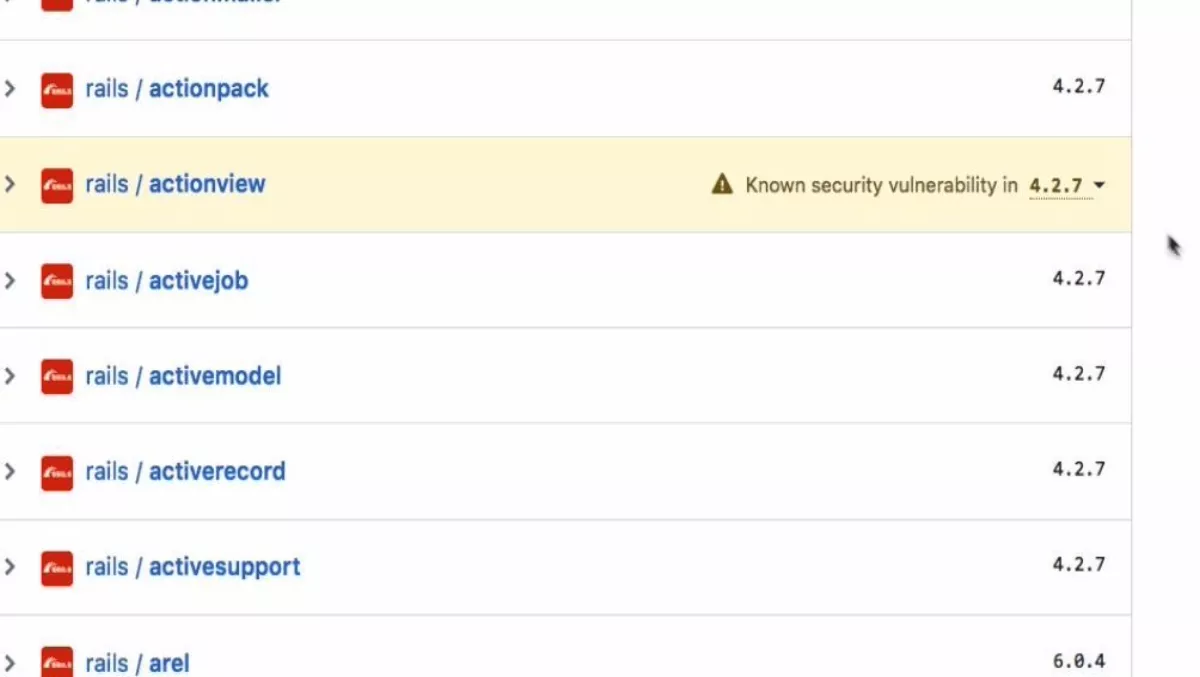
The company has now created a dependency graph that allows developers to track which other projects they are using in their work, and which of their projects other developers are using – all without leading their repositories.
" Now, our data can help you manage increasingly complex dependencies and keep your code safer as you work on connected projects—even for private repositories," the company states in a blog.

Eventually, the dependency graph will track when dependencies are open to public security vulnerabilities. The company will notify those affected and may suggest known security fixes.
Security alerts are the first in what we hope will be a robust collection of tools to keep your code safe, and we need people who build on our APIs to help us make them even better —and to keep security data current for the community," the company says.
GitHub also revamped the way it allows users to discover and contribute to new projects.
Its news feed has been updated to include 'discover repositories' that show recommendations for open source projects tailored to users based on their own preferences and popular GitHub projects.
The 'Explore' experience has also been curated to show collections, topics and resources from contributors worldwide.

"Collections are hand-picked resources from the GitHub universe and beyond. Browse collections to learn about ideas that interest you, like machine learning or game development, and find repositories and organizations that help you dig deeper," the company says.
"Topic pages help you find projects related to technologies, languages, frameworks, or platforms—thanks to the GitHub community's topic tags. Use topic pages to find all Android or CSS projects for example, and suggest edits to topic pages in our public repository.
GitHub will also be introducing premium support for GitHub Enterprise customers. It is also working on a new community forum, marketplace trial program and a team discussion tool.
In 2017, GitHub hosted 24 million developers; 67 million repositories and 1.3 million students learning on the platform, according to its Octoverse report.
GitHub Universe wraps up today in San Francisco.


