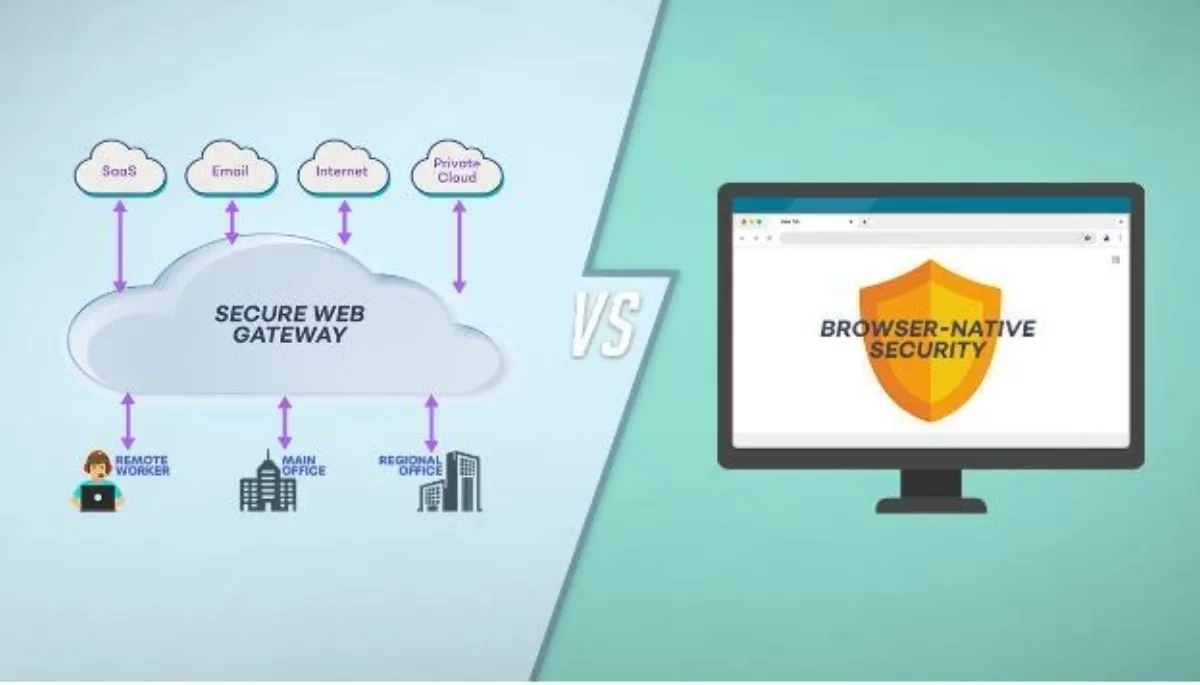
Why is a browser-native security solution better than cloud-based SWGs?
Over the last twenty years, corporate security strategies have merely shifted from on-premises Secure Web Gateways (SWGs) to cloud-based services, resulting in an increased dependence on data centres, primarily to support remote workers. This shift creates inefficiencies and security risks as user traffic is rerouted through potentially distant data centres, affecting web browsing reliability, performance, and privacy.
In contrast, companies like SquareX are building browser-native security solutions that offer a more direct, context-aware, and efficient approach, adept at handling intricate web interactions and detecting multi-layered threats, thus presenting a compelling alternative to the outdated SWG model.
Let's start by examining the challenges associated with cloud-based SWGs. A primary issue is the single chokepoint for traffic. All traffic is directed through a centralised point, which can lead to potential bottlenecks and reduce efficiency. Additionally, outages at data centres can cause web pages to fail to load, disrupting user access and productivity. The traffic routed through these proxies also suffers from a compromised reputation, which frequently leads to being blocked. There are also geographical and network-specific restrictions that can hinder the use of proxies in certain areas. Lastly, the consolidation of documents and data passing through an SWG provider raises the risk of privacy breaches due to potential insider attacks.
How does a browser-native solution overcome the above challenges and also give a force-multiplier in security and privacy?
Enhanced Web Application Context Awareness
Browser-native security solutions excel in understanding complex web applications since they operate within the browser. They can closely monitor user interactions, website code, and data rendering, which is crucial for identifying sophisticated attacks. In contrast, traditional server-side proxies struggle with these tasks, especially in rich, client-heavy applications that dynamically update from the server and modify client-side rendering. This complexity makes it hard for them to distinguish between requests triggered by user actions and those from malicious scripts.
Superior Detection of Multi-Layer Threats
Multi-layer attacks traditionally require analysis by an SIEM to correlate data and draw conclusions. However, cloud-based proxies, which only analyse surface-level code and data, fail to detect deeper attacks. Browser-native solutions, with agents operating directly within the browser, can process a wide range of signals locally, enhancing threat detection as it occurs.
Enhanced Upstream Threat Detection
Browser-native systems excel at early threat detection, monitoring data before it even reaches device storage and preventing malicious files from causing damage. This pre-emptive action is advantageous over-relying on traditional endpoint security solutions like anti-virus software, which only acts after files have been downloaded.
Zero Lag Attack Mitigation
One of the key advantages of browser-native security is its ability to immediately respond to threats directly at the source without the delays inherent in cloud-based systems that process data remotely.
In summary, browser-native security solutions offer a more nuanced and effective approach to cybersecurity. Their ability to understand complex web interactions, detect multi-layer threats, provide upstream threat detection, and ensure zero lag in threat mitigation makes them a compelling choice over traditional cloud-based secure web gateways or proxies. As cyber threats become more sophisticated, the need for equally advanced security solutions becomes imperative, and browser-native solutions are well-positioned to meet these challenges.
The future of web browsing security will rely on the browser to natively take a more active role in detecting and mitigating threats.