
4 Ransomware trends to watch in 2019
At the end of each year for the last two years, I have written articles predicting trends in ransomware for the next coming year. Each article was a mix of accurate and inaccurate predictions — fortunately, more accurate than inaccurate.
In 2018, the division between the "haves" and "have nots" of ransomware campaigns continued to grow. The "haves" — ransomware actors who continued to make a lot of money and successfully exploit many targets — focused on health care and government (or quasi-government agencies) and these actors avoided traditional phishing or web exploitation campaigns.
The biggest ransomware story of 2018, arguably, happened in the city of Atlanta. The SamSam team hit the city hard, disrupting vital services for days and leaving some data completely unrecoverable. But Atlanta wasn't the only city or state government hit. There were dozens of stories about cities, utilities, ports, and more that were infected with ransomware in 2018.
Since ransomware attacks continue to challenge all types of organisations (and not just health care and government), here are the anticipated trends in ransomware for 2019.
1. The ransomware market will continue to grow, but few campaigns will have impact
In January of 2017, Recorded Future was tracking 635 ransomware campaigns. In February of 2018, that number was 1,105, and at the end of January 2019, we are tracking 1,463 campaigns. While the number of ransomware variants continues to expand rapidly, the truth is that most of these campaigns are ineffective and die out quickly.
An example of this phenomenon is the Cryptgh0st ransomware shown below. It was first discovered in May 2018 and by the end of August, virtually all mentions of the ransomware disappeared. Cryptgh0st does not appear to have been widely deployed on victim machines, and the Bitcoin wallet associated with the campaign only shows two incoming transactions — one for about $370 and a second for $6.
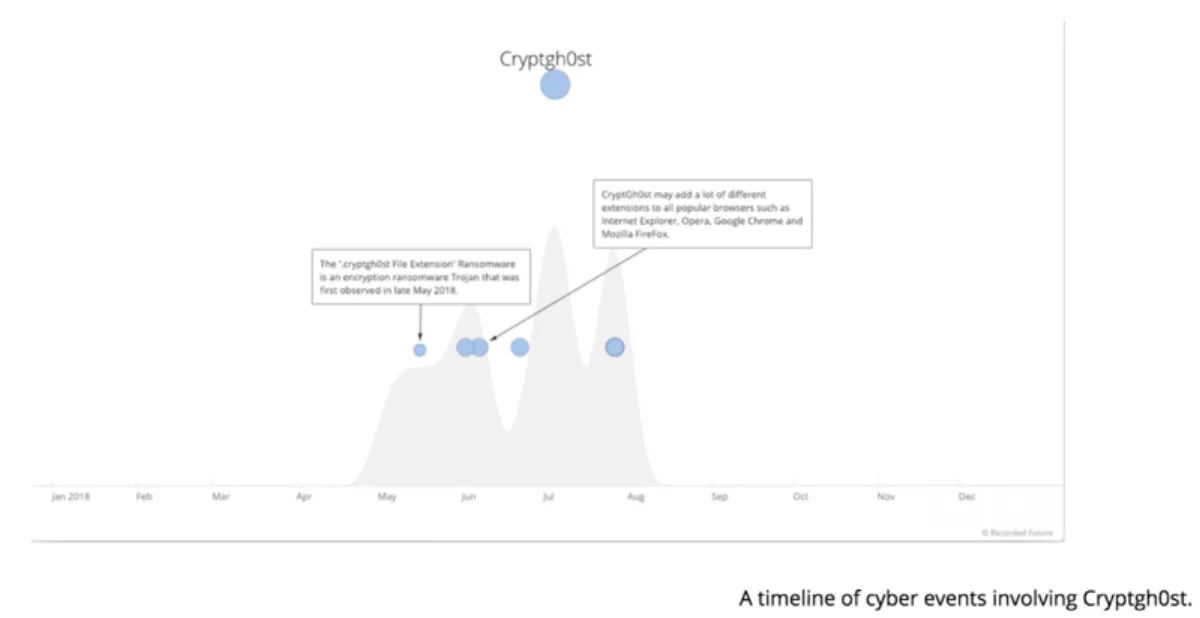
There are dozens of ransomware campaigns that follow a similar pattern, where the biggest noise comes from the fake "how to remove X ransomware" websites, but they generate very little real threat.
2. Successful ransomware campaigns will continue to rely on open RDP
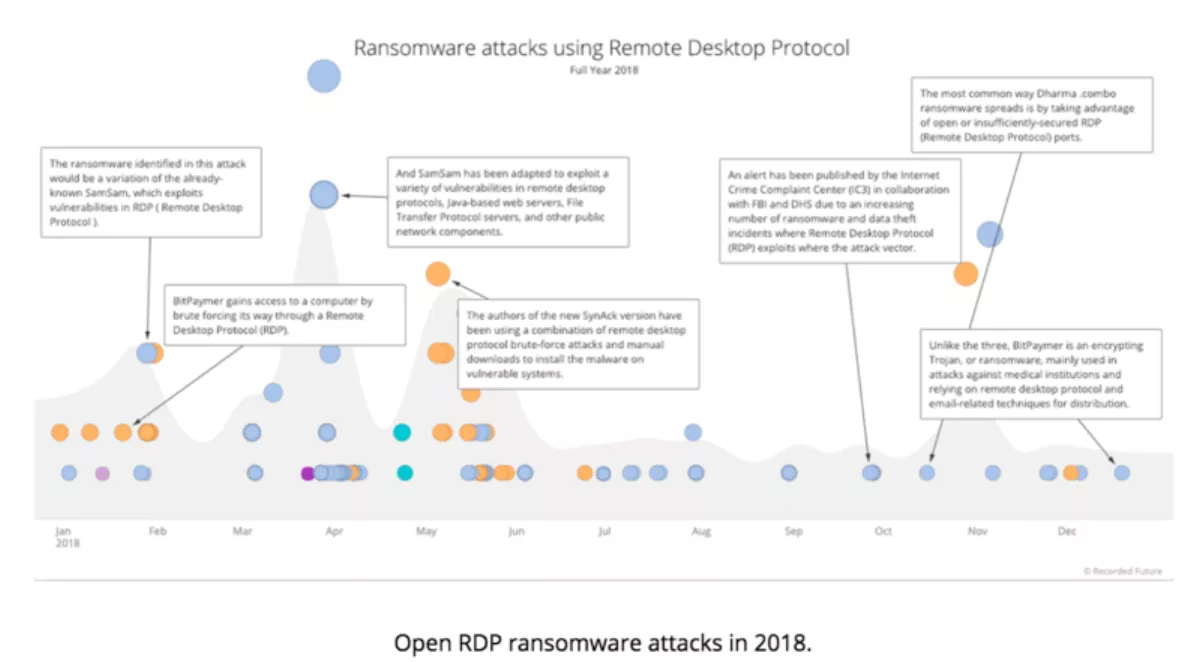
Most successful campaigns in 2018 involved ransomware that relies on open Remote Desktop Protocol (RDP) servers as the initial access point. Ransomware families such as SamSam, BitPaymer, and CrySiS thrived, whereas other campaigns failed because they did not rely on web exploitation or phishing to gain access to victim networks.
These campaigns look for networks that have internet-facing servers running the RDP service. Attackers either take advantage of well-known vulnerabilities in unpatched servers or use a brute-force password attack (trying common login names, such as "administrator," along with thousands of common passwords to gain access). Once the attackers have successfully gained access to the exposed system, they use it as a jumping off point into the core of the network, installing their ransomware onto target machines and often disabling backups and other protections.
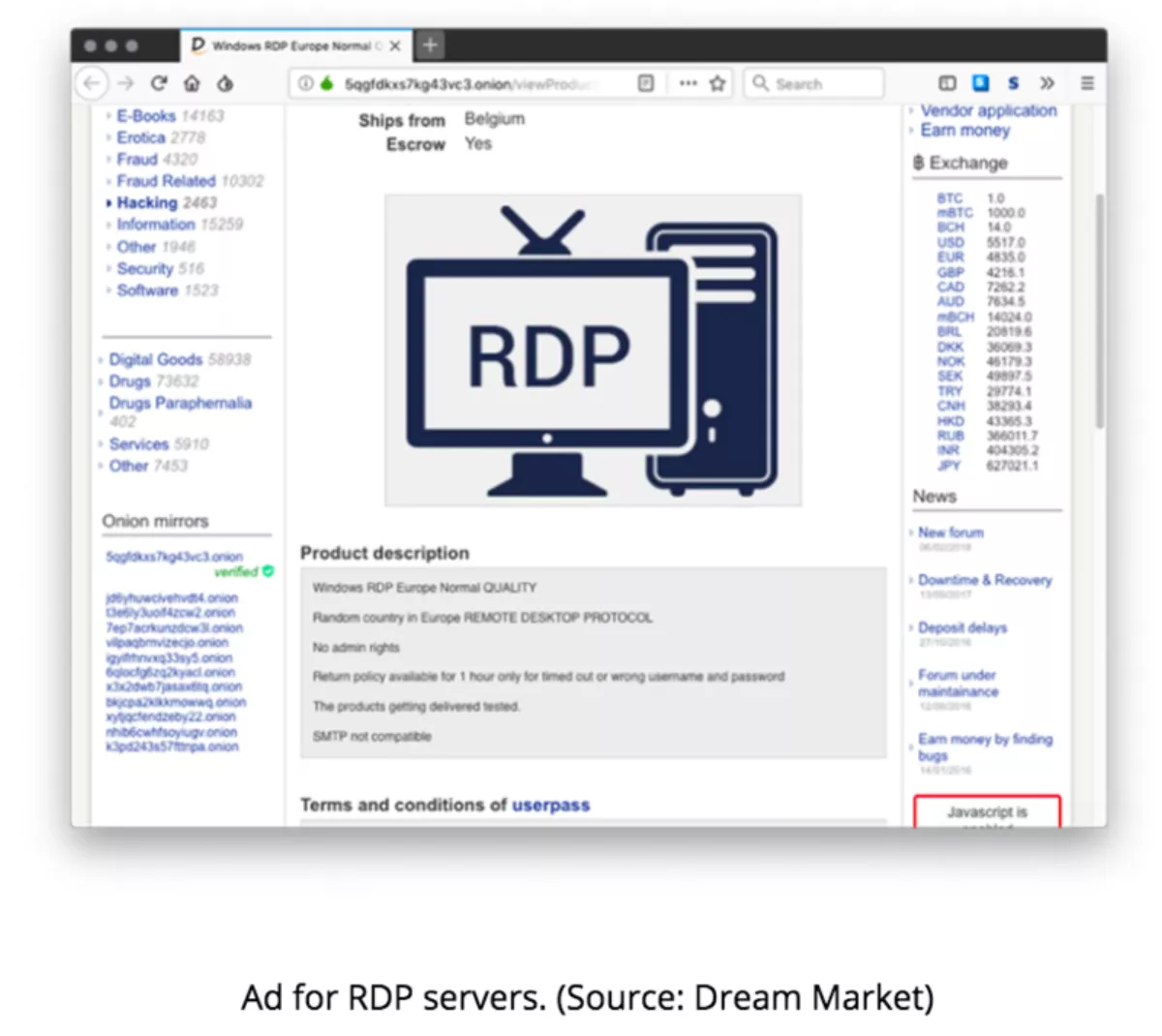
Of course, it's not just RDP that these attackers use. As seen with SamSam, CrySiS, and BitPaymer, attackers look for any service that may give them access to the core of the network. JBoss, FTP, and other services have all been targets of these groups, but open RDP servers are the preferred target because there are a lot of them, they are easy to find, and they are easy to exploit. Even better, if an attacker is having trouble exploiting open RDP servers, they can just purchase access on underground markets for about $15, as shown below.
Publicly accessible RDP servers are widely available for a couple of reasons. The first is that many organisations use RDP instead of a VPN to gain remote access to their work or home machines. The second reason is that often organizations are not aware that the RDP service is running on internet-facing servers. This could be a configuration error, a failed security check, or it could be started by another service after the server is deployed.
It is worth noting that with the recent takedown of the xDedic marketplace, the pool of readily available, low-priced, RDP servers may be in short supply, at least until a new dominant marketplace emerges. That won't slow down the more sophisticated ransomware teams who scan and infect their own RDP servers, but it may impact some of the less sophisticated campaigns.
Almost every headline-grabbing ransomware story in 2018 involved criminals who accessed the victim networks through a poorly secured RDP server, as shown in the timeline below. Note how the trend line stayed consistent throughout the year. Expect that to continue into 2019, at least until organisations figure out how to secure or remove their RDP servers.
3. GandCrab will continue to ignore this list and somehow be successful
The exception to the first two trends on this list continues to be GandCrab ransomware — one of the few widely deployed ransomware campaigns. The GandCrab team eschews RDP for phishing and exploit kit-based campaigns. GandCrab ransomware was first reported at the end of January 2018, and since then, the team behind GandCrab has made dozens of adjustments and at least five new code releases.
The GandCrab team is very responsive to security researchers, often including references to reports about their ransomware and how the team has adapted to those reports in their underground ads. Delivered primarily via phishing campaigns (though they also use exploit kits), the GandCrab team relies heavily on Microsoft Office macros, VBScript, and PowerShell to avoid detection, but will often incorporate new means of exploitation and avoidance as proof-of-concept code is released.
GandCrab uses a ransomware-as-a-service (RaaS) model to maximise delivery and focuses primarily on consumer delivery, with ransom demands ranging from $500 to $600. Although consumer tools such as free mail services and anti-virus vendors have gotten better at detecting ransomware, GandCrab continues to find success, as shown in the timeline below.
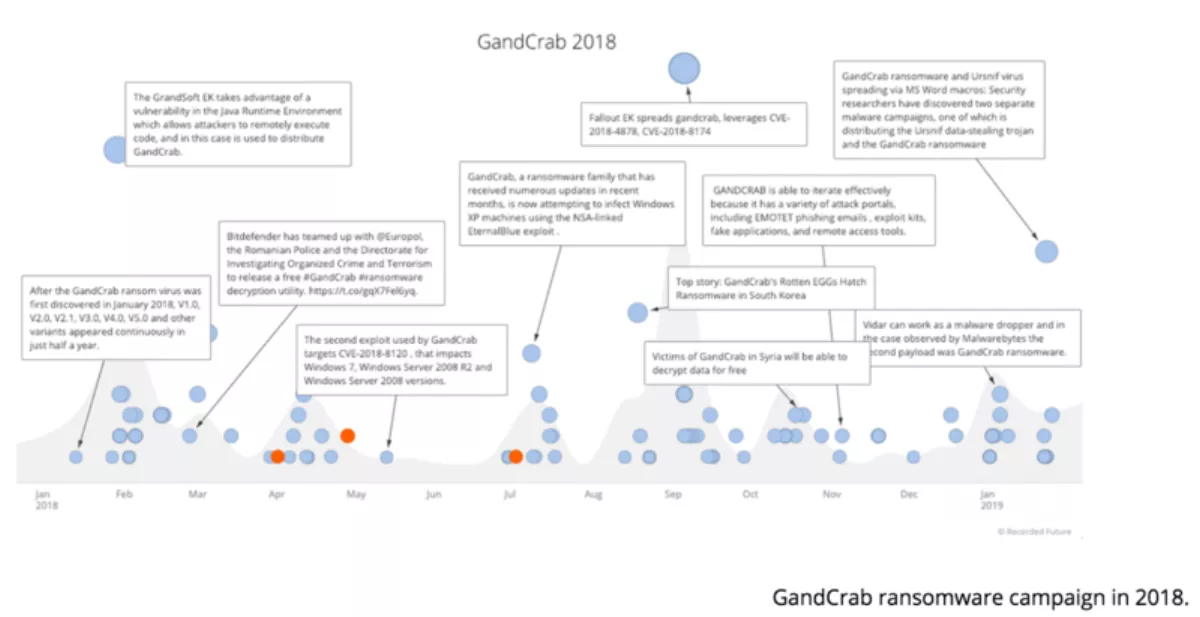
The team behind GandCrab doesn't appear to be slowing down at all, so expect to see more from them in 2019.
4. Nation-states and cybercriminals will continue to blend ransomware attacks
2018 saw the rise of nation-state threat actors using cryptocurrency mining and ransomware campaigns as a way to generate revenue for the state or distract from other activities. Ransomware was not only used as a distraction or destruction tool, but also as a money-making tool.
This trend will continue in 2019, especially with countries that are heavily sanctioned — however, the twist is that these countries will use the same ransomware tools that the criminals are using so that they blend in with all of the other campaigns.
As shown in the timeline below, Hermes ransomware was originally marketed on Russian forums and used by cybercriminals. The Lazarus group, which is linked to North Korea, has also used the Hermes ransomware in at least one attack.
When Ryuk ransomware first appeared in late 2018, many researchers assumed it was tied to North Korea as well because Ryuk ransomware shares much of its code base with Hermes ransomware. However, further research determined that the Ryuk actors are most likely located in Russia and they had built Ryuk ransomware using (most likely stolen) Hermes code.
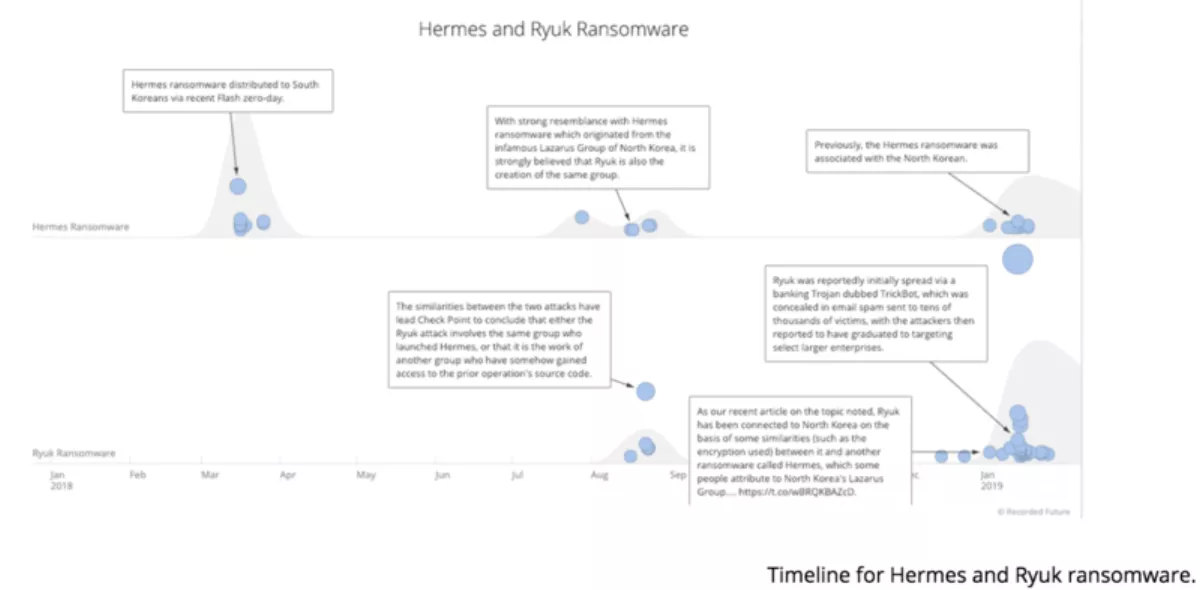
As ransomware actors become more sophisticated, the code stealing (or sharing) will become a two-way street, and nation-state actors may very well use cybercriminal code to build their ransomware variants.
Conclusion
One thing that has held true through the rise, the plataeu, and slipping of ransomware campaigns is that the most successful ransomware actors are very nimble and quickly adapt their techniques to the changing security landscape.
Many organisations have put in phishing countermeasures and are still cautioning those users on their network to watch for phishing-based ransomware attacks. This is not necessarily bad advice, but as successful ransomware actors migrate to other means of access, these protections become less effective against ransomware.
Just as ransomware teams adjust their attacks based on the changing security landscape, security teams need to be able to adjust their focus and protections. Understanding what techniques are being used by ransomware actors allows security teams to be more responsive to the current threats and adapt their protections to keep their organisation safe.

