
Minimising the impact of REvil delivered via Kaseya servers
As the United States prepared for a holiday weekend ahead of the Fourth of July, the ransomware group REvil was capitalising on a vulnerability in Kaseya software to attack managed service providers (MSPs) and their downstream customers. At least 1,500 companies appear to have been affected, even ones with no direct relationship to Kaseya.
REvil has demanded a total payment of $70 million in Bitcoin. For a group that tries to maximise its profits, this seems odd for two reasons:
- How does the group expect a single entity to collect $70 million from potentially thousands of affected organisations? REvil must be aware of the massive logistical challenges behind this, even if they expect Kaseya to act as a focal point for collecting the money.
- Since DarkSide lost access to most of the Colonial Pipeline ransom, criminal groups have shifted to demanding payments in Monero rather than Bitcoin. As a cryptocurrency, Monero appears to be more difficult to track for law enforcement agencies. The fact that REvil used Bitcoin, a more traceable cryptocurrency, seems counterproductive to their usual goal of maximising profits.
Darktrace also noticed that other, more traditional 'big game hunting' REvil ransomware operations took place over the same weekend. This is not surprising as REvil is running a RaaS model — so it's likely some affiliate groups continued their regular big game hunting attacks while the Kaseya supply chain attack was underway.
Dissecting REvil ransomware from the network perspective
The attack was particularly effective because it leveraged unpatched vulnerabilities in Kaseya systems, which were able to bypass signature-based security. Once Kaseya had been infected, REvil were able to compromise almost 70 MSPs leading to a ripple effect down the supply chain. As the malware came from trusted third parties, it easily evaded legacy security tools.
Darktrace, however, takes a fundamentally different approach to security. It applies Self-Learning AI to form an understanding of 'normal' for every user and organisation. This enables it to detect anomalies and stop threats on the first encounter.
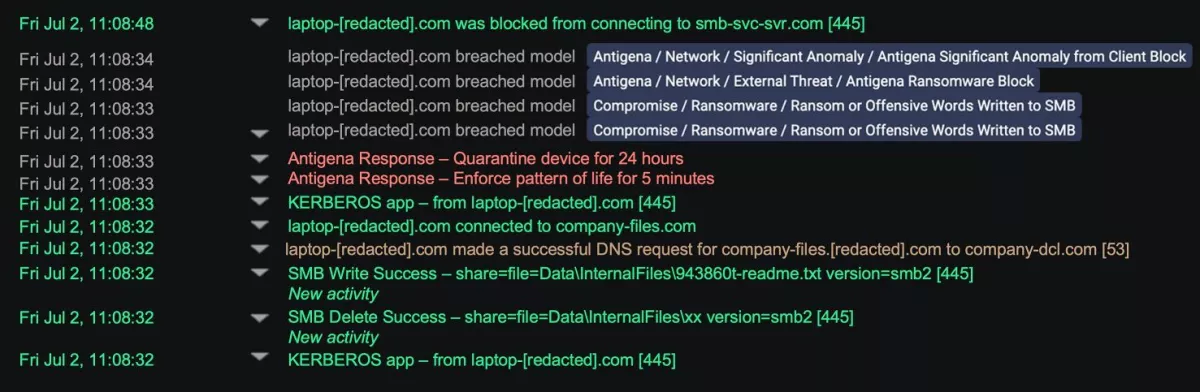
Figure 1: Darktrace detects encryption from the infected device
Darktrace detected the first signs of ransomware on the network as soon as encryption had begun. The ransomware began to take action at 11:08:32, shown by the 'SMB Delete Success' from the infected laptop to an SMB server. While the laptop sometimes reads files on that SMB server, it never deletes these types of files on this particular file share, so Darktrace detected this activity as new and unusual.
Simultaneously, the infected laptop created the ransom note '943860t-readme.txt'. Again, the 'SMB Write Success' to the SMB server was alerted as a new activity. By detecting and correlating these subtle anomalies, Darktrace identified them as the earliest stages of ransomware encryption on the network.
Antigena, Darktrace's Autonomous Response capability, took immediate action by enforcing a 'pattern of life' for five minutes and quarantining the device for 24 hours.
For several minutes, the infected laptop kept trying to connect to other internal devices via SMB to continue the encryption activity. It was blocked by Antigena at every stage, limiting the spread of the attack and mitigating any damage posed via the network encryption.
Unpredictable is not undefendable
This case study demonstrates how self-learning technology detects such attacks and minimises damage. It functions as a crucial part of defence-in-depth when other layers — such as endpoint protection, threat Intelligence or known signatures and rules — fail to detect unknown threats.

