Bybit: when hackers target people, not systems
This past month, hackers stole a staggering $1.5 billion from the crypto exchange Bybit in what the market dubbed "The biggest digital heist ever". Unsurprisingly, the sheer scale of the attack has led many to once again question the safety of crypto, with critics pointing fingers at the industry's security vulnerabilities. But here's the twist: the wallets did their job. The problem wasn't a failure of the underlying technology - it was a failure of 'human' security.
What exactly went wrong?
The bottom line is that the Bybit hack wasn't a failure of blockchain security - the attackers didn't crack an impenetrable system; they manipulated people…
In very simple terms, the attack occurred when the company was making a routine transfer of Ethereum from an offline 'cold' wallet (a highly secure, offline storage solution designed to protect assets from cyber threats by keeping private keys completely disconnected from the internet) to a 'warm' wallet (a semi-online wallet used for operational liquidity, allowing faster access to funds while maintaining some security measures) for daily trading activities.
The hackers gained access to the software account that helps Bybit control these transfers by compromising a developer's machine. They remotely modified the user interface, injecting malicious code that manipulated the wallet's transaction approval process. Employees who usually sign off these transfers saw what looked like legitimate transactions, but behind the scenes, the attackers rewrote the rules, diverting funds straight into hacker controlled accounts.
To make matters worse, the attack leveraged 'blind signing'. When approving the transactions, employees were effectively signing off on something they couldn't fully see on their screen. The attackers manipulated this process so effectively that employees believed they were approving routine transfers.
The combination of UI manipulation and blind signing created a near-perfect deception. Importantly, however, it wasn't crypto's technology that failed. It was a case of catastrophic human error.
Can the funds be recovered?
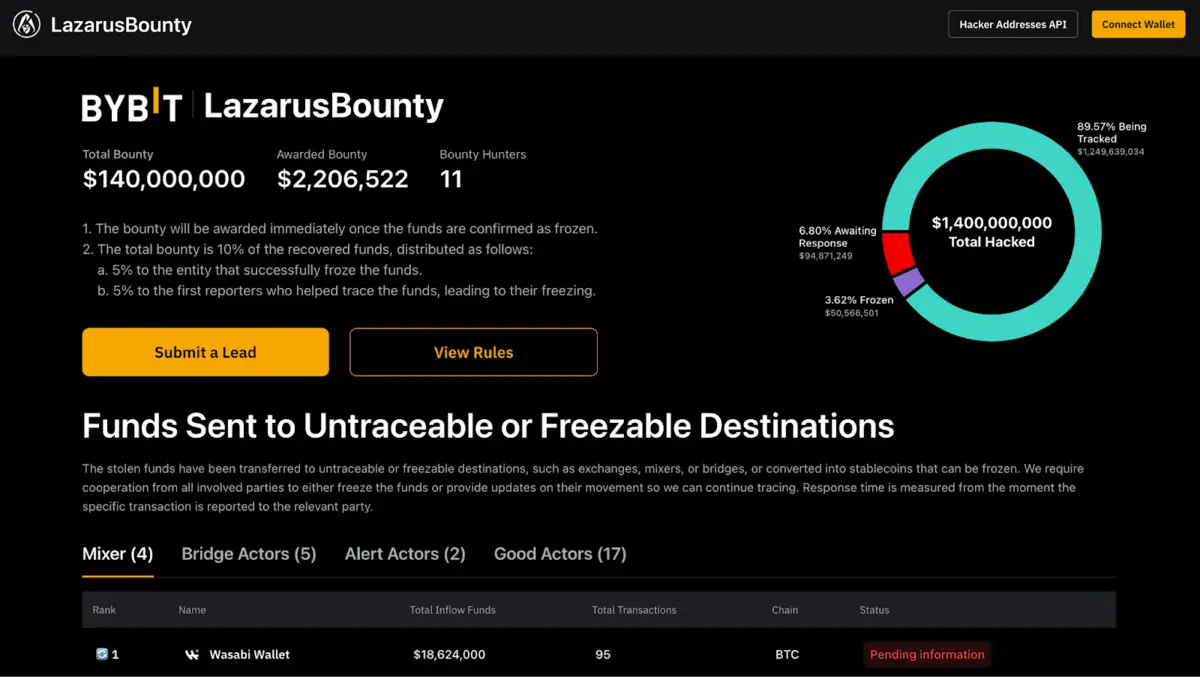
The hack has been attributed to North Korean state-sponsored hacking group the Lazarus Group who has a history of targeting crypto exchanges to fund North Korea's economy and sanctioned programs.
Working against this group is the traceability of blockchain. With all eyes on the stolen funds and every blockchain transaction publicly visible, being able to bank the money will be as difficult as stealing it in the first place (although some funds have also been converted into privacy-focused coins like Monero, which are much harder to track).
Importantly, Bybit acted swiftly to reassure customers and worked quickly to secure emergency funding to restore liquidity. They've also launched a comprehensive bounty program offering 5% rewards to individuals or firms that help identify and freeze these stolen funds. A real-time leaderboard has been set up to track progress, turning crypto sleuths into heroes!
Preventing future attacks
If there's one takeaway from this attack, it's that the industry needs stronger protections against cyber crime - including human-targeted cyber crime..
Exchanges need to go beyond traditional security - The danger of 'blind signing' has been made clear and needs to be phased out in favor of clear transaction signing so users can actually see what they're approving.
In addition, multi-factor authentication for this type of signing could be enabled if exchanges opt to use multi-party computation (MPC) wallets which have started to gain favour in many circles over seed phrases, making key compromises far more difficult. MPC wallets distribute private key 'fragments' among multiple parties, reducing the risk of a single point of failure. Unlike traditional seed phrases, MPC eliminates the risk of a single exposed key leading to complete account compromise. (Easy Crypto's wallet is an MPC wallet.)
Employees need better training - Cyberattack drills should be routine and phishing awareness training should be ongoing. Attackers are getting smarter and exchanges need to ensure their teams can recognise a red flag before it's too late.
Real-time monitoring needs to be the standard - AI-driven security systems can flag unusual transaction patterns instantly, triggering immediate reviews and helping prevent unauthorised withdrawals.
The bigger picture
This hack didn't expose flaws in blockchain itself - but it did expose the risks of human error and deception. That distinction, however, didn't make much difference to the general public. The damage was done, and confidence in crypto security took yet another hit.
Hackers will keep coming…The real question is whether the crypto industry will learn from Bybit and act now to prevent the next attack? If they don't, it's only a matter of time before another billion-dollar breach shakes the market all over again.

