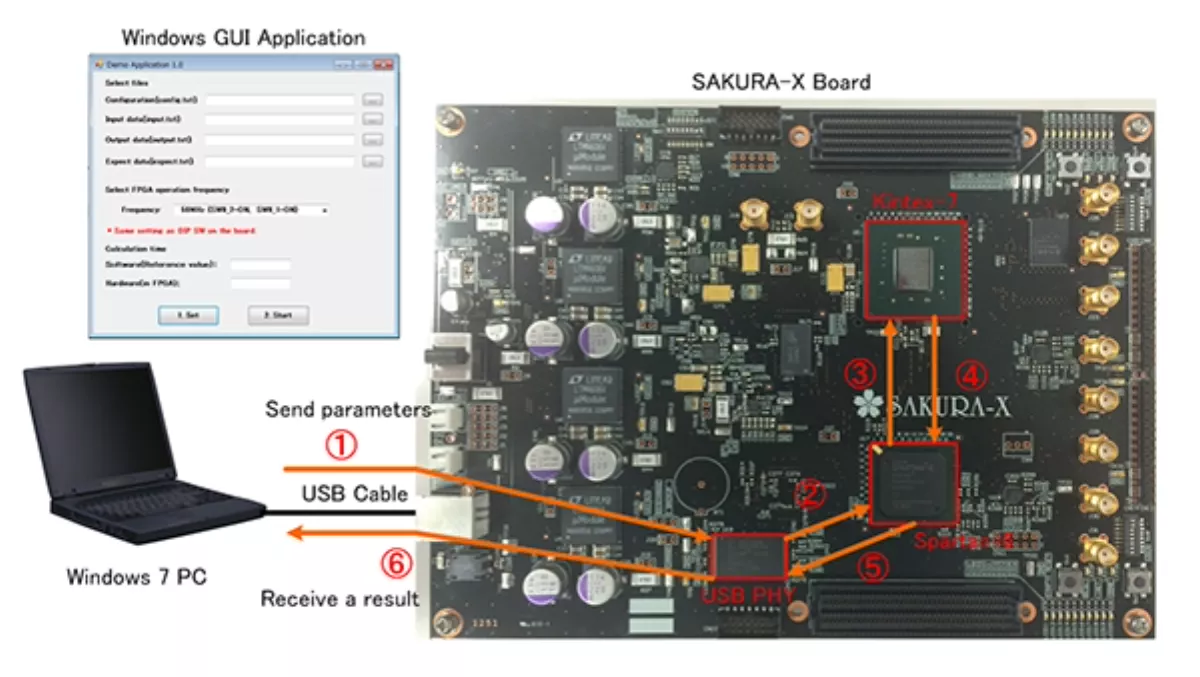
Secure cryptoprocessors are getting more advanced, and now there is a world-first in adjustable security, according to researchers at Okayama University and Tokyo Electron.
The secure cryptoprocessors now have the ability to adjust security levels without adjusting the processor itself.
University researchers have developed the adjustable and secure cryptoprocessor that supports both eliptic curve and pairing-based cryptographies.
The researchers say that the cryptoprocessor will have wide-ranging implications for IoT devices and 'ubiquitous terminals' because of its size and power capabilities.
This will provide scalable control, supported by cyclic vector multiplication algorithm, or CVMA. The algorithm is most commonly used for vector multiplication but also has wide uses for security scalability.
The researchers believe IoT and cloud trends will continue to need public key cryptography for security. Elliptic curve cryptography is particularly important for device and user authentication.
However, the researchers also state that computer performance is also on the increase, but that doesn't mean it's any easier to adjust device security.
They say this is because public key cryptography uses complex mathemetical problems, which can be difficult to program for security adjustment.
While traditional RSA cryptography key length has increments of 512, 1024, 2048 and 3072 bits, processors and their mathematical bases need to be upgraded.
The new secure cryptoprocessor offers security strength range from 256-5120 bits through a small circuit area size and 'practical calculation efficiency'.
